IoT Devicemanagement Client - awsclient
Sections of this page
This is our main component. It is written in C++ and can be compiled to many targets.
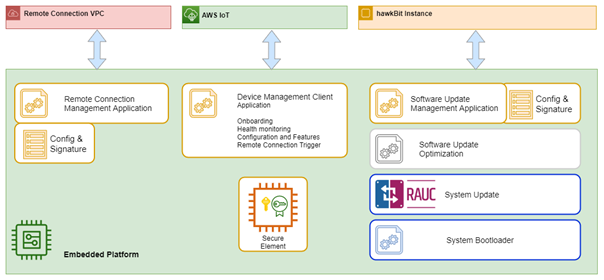
Purpose
Mutual authentication to our AWS Back End
Mutual TLS using x.509 Certificates
Hardware key storage (see below “Hardware Security“) or file-based keys are supported
Automated onboarding and zero-touch provisioning
The device can itself register to the backend and will be recognized just in time
after this, all configurations and server onboarding in the backend is triggered
after that, all needed configuration files will be downloaded in place so all other applications like Remote Manager Client or Rauc Hawkbit Updater a function
Transmit local health and system parameters
Example datapoints are:
Linux disk space status
SW version information
RAUC information
Serial Number, MAC and Hardware Type
SIM ICCID Numbers
VIN (Vehicle Identification Number)
Available networks coverage
system status
…
datapoints can be adapted by the customer in the configuration file
Deployment of files - (!= Software Update)
Used for files, configurations, parametrization, licenses can be deployed to each device individually
Security
Explicit allow-lists to specify which files and folders can be used
Non-listed files and folders will be rejected
Triggering remote commands and scripts
pre-defined jobs, tasks, scripts, … can be triggered by the back end
when the iot-client receives the trigger, it executes the required task
return codes will not be propagated to the backend, as this might lock control flow
Security
Explicit allow lists specify which binaries, scripts, … can be called
Non-listed calls will be rejected
Log 2 Cloud
Any application can log to a buffering local SQLite DB
Log entries are then transferred to the backend
Binary Information
Our client can be delivered as a pre-compiled binary. Alternatively, our customers can compile it from source.
Size: ~ 900kB
Common locations:
PHYTEC: /usr/bin/awsclient
BHtronik: /usr/bin/awsclient
Usage
For periodic calling via systsemd
systemctl start awsclientExample: /lib/systemd/system/awsclient.service
[Unit]Description=OSB AWS ClientAfter=network.target[Service]User=rootEnvironment="OPENSSL_CONF=/etc/ssl/opensslA71CH_i2c.cnf"ExecStartPre=/bin/ping -c 3 -w 7 aws.amazon.comExecStart=/usr/bin/awsclientWorkingDirectory=/config/os/aws/TimeoutStartSec=15mRestart=on-failureRestartSec=1m[Install]WantedBy=multi-user.targetExample: /lib/systemd/system/awsclient.timer
[Unit]Description=Timer for executing OSB AWS Client periodically[Timer]OnActiveSec=1mOnUnitActiveSec=5m[Install]WantedBy=basic.targetExample: /etc/systemd/system/basic.target.wants/awsclient.timer
[Unit]Description=Timer for executing OSB AWS Client periodically[Timer]OnActiveSec=1mOnUnitActiveSec=5m[Install]WantedBy=basic.targetConfiguration Options
See separate awsclient configuration page for details
Hardware Security
Our client supports OpenSSL and we support the use of:
Secure Elements
Trusted Platform Modules TPM
TPM 2 modules of other vendors should be compatible, as TPM is a standard https://de.wikipedia.org/wiki/Trusted_Platform_Module
Dependencies
curl glib-2.0
glib-2.0-native
json-glib
openssl
sqlite3
Origin and License
AWS SDK for connecting to AWS IoT from a device using C++ used as basis
It is licensed under the Apache 2.0 License
Open Source Information
As not required by the Apache 2.0 License our adaptions to the AWS project are not publicly available yet.
![]() Nevertheless, our clients and integration partners get full access to our source repo to be able to inspect and build the components on their own.
Nevertheless, our clients and integration partners get full access to our source repo to be able to inspect and build the components on their own.